Operating system fingerprinting on the data plane
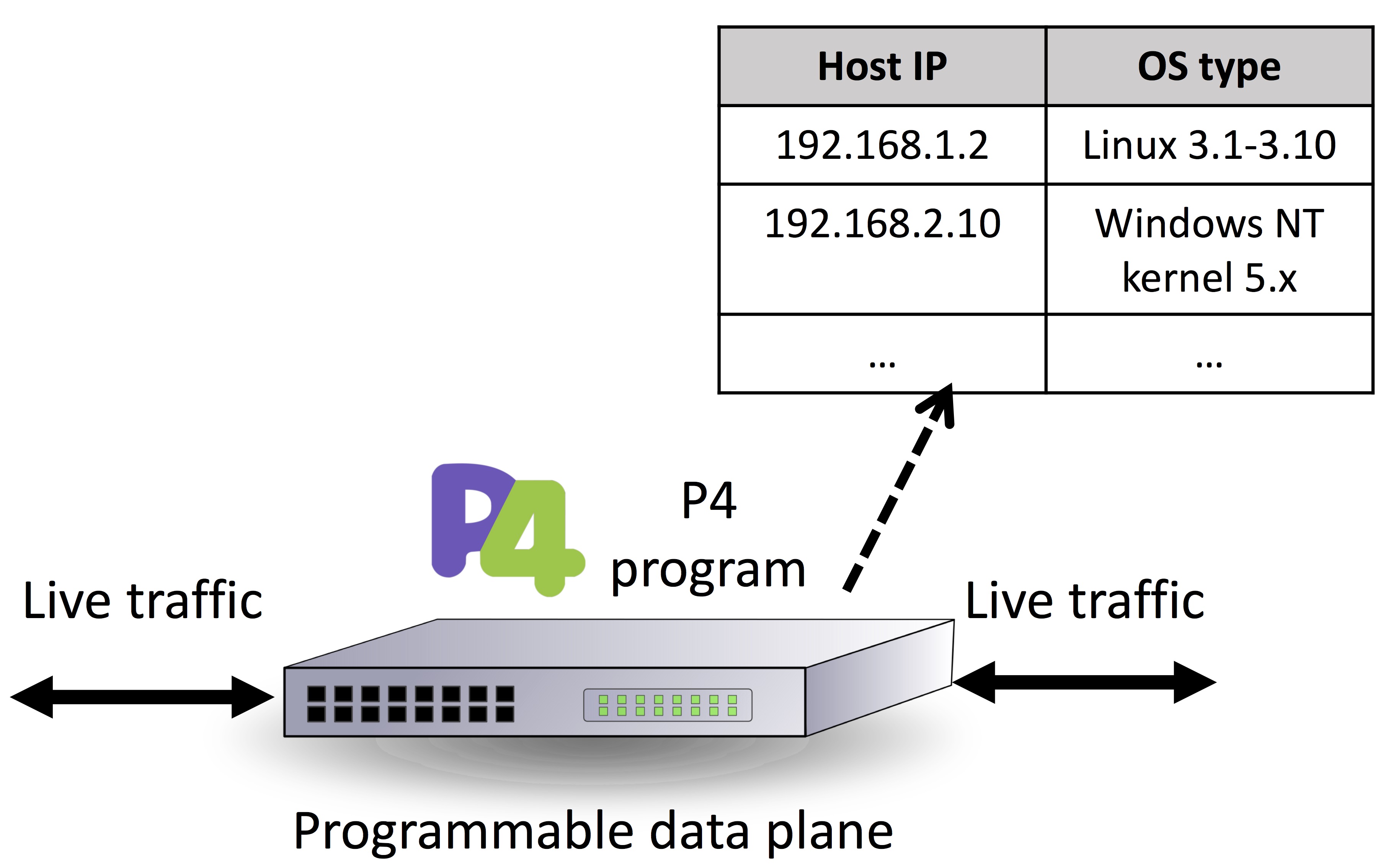
Information of operating systems running on end-hosts is valuable when managing an enterprise network. Such information helps network administrators maintain an accurate device inventory, apply access control policies based on OS types, detect outdated OS and plan upgrades, or even detect the source of spam emails.
However, collecting OS information from every host in the network is difficult. Manual input from users is cumbersome and inaccurate. Several existing OS fingerprinting tools rely on sending active probes, which incurs additional load on the network. Passive OS fingerprinting tools, such as p0f, are more efficient, but a software tool cannot keep up with the amount of traffic and bandwidth of today's networks.
We provide a passive OS fingerprinting solution that runs on programmable data plane. This can identify the operating system of end-hosts that are active in a network in real time by passively monitoring live traffic. It also performs OS fingerprinting in line-rate, without introducing any additional latency.
Code for BMv2
GitHub RepoCode for Tofino
We are still working on a code that runs on the Barefoot Tofino switch.
Project lead
Sherry Bai (sb16@alumni.princeton.edu)
Hyojoon Kim (joonk@princeton.edu)
Jennifer Rexford (jrex@cs.princeton.edu)
Publications
-
Passive OS Fingerprinting on Commodity Switches
[ paper (pdf) ]
Sherry Bai, Hyojoon Kim, and Jennifer Rexford
Princeton Computer Science Technical Report TR-010-19, September 2019.